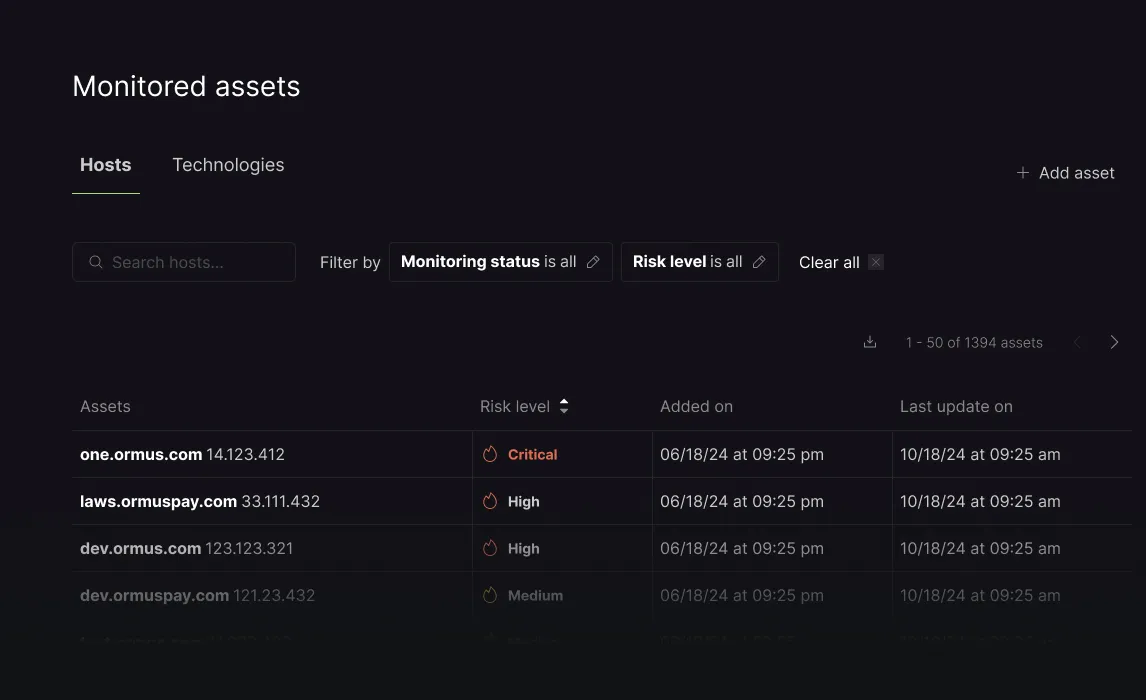
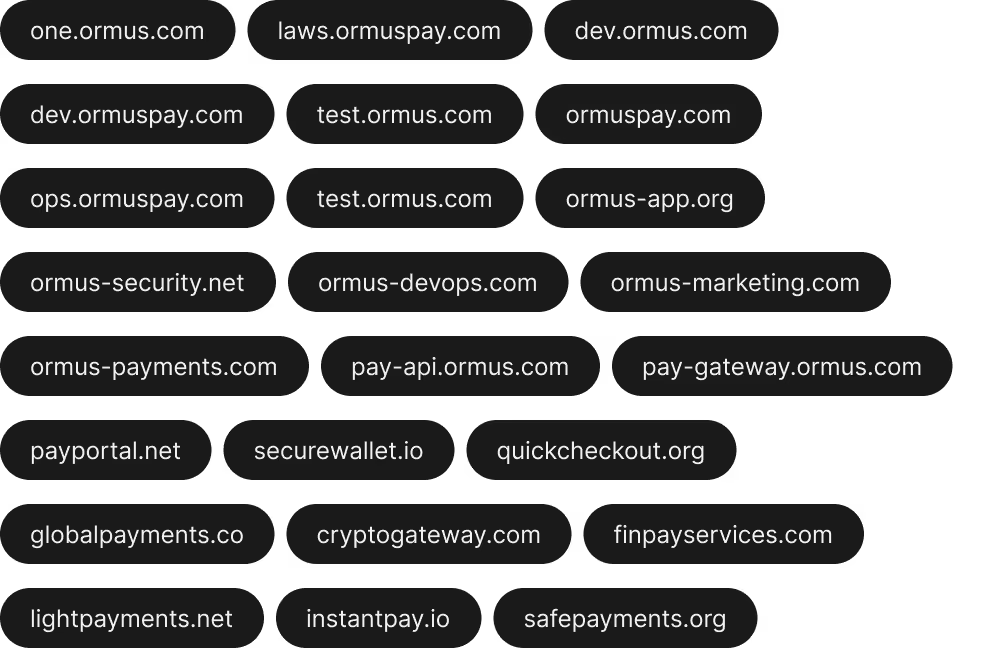
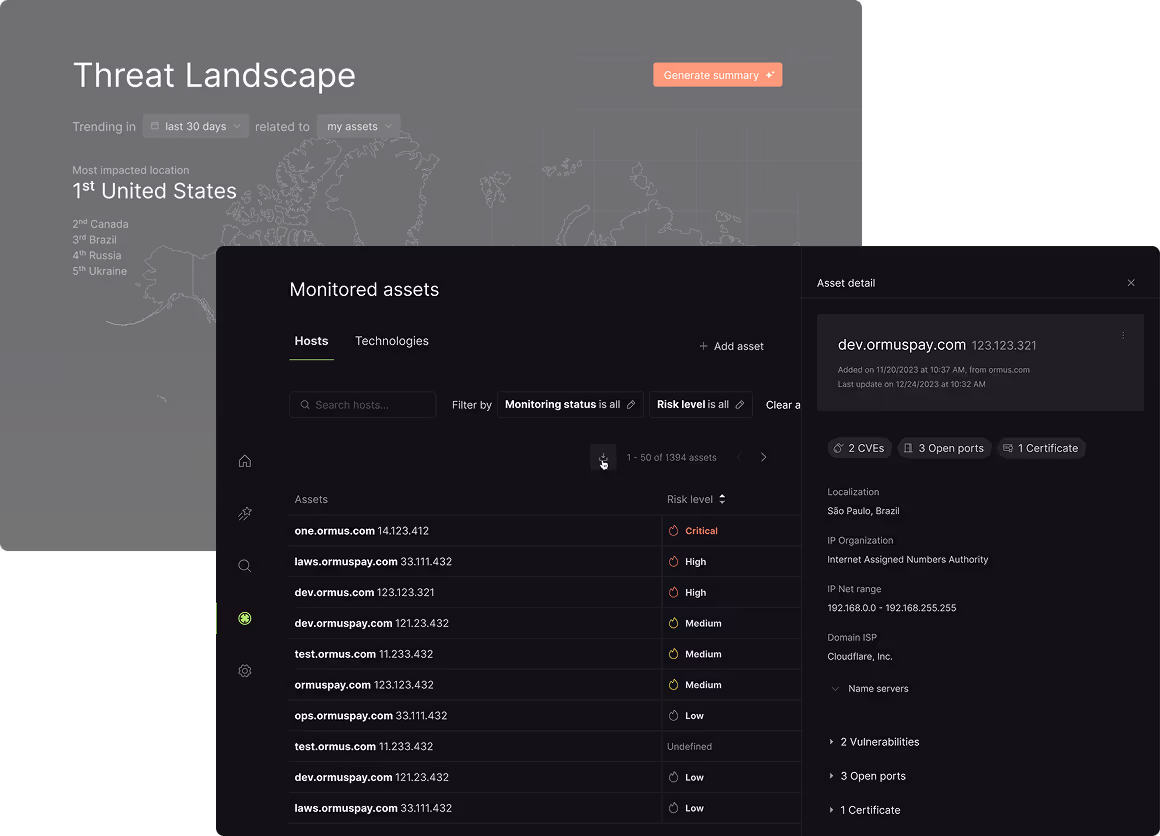
EASM is a solution that identifies, monitors, and evaluates digital assets exposed on the internet. It helps your company reduce risks by discovering servers, domains, subdomains, APIs, and cloud applications that may be vulnerable, including those not officially cataloged (shadow IT).